Hello there! My name is Terin Williams and I am the Cyber Security Advisor assigned to Ohio (based in Columbus) for the Department of Homeland Security (DHS) Cybersecurity and Infrastructure Security Agency (CISA). I had the opportunity to speak at CIFT’s Ohio Food Industry Summit back in April and I’m happy to continue to share some of my expertise with this guest blog. Ultimately, I credit God with my move to cybersecurity, but the military pushed me towards cybersecurity and away from medicine. I just knew I wanted to help people, but cybersecurity wasn’t a thing when I went to college.
Cybersecurity vs. IT
The military did what many others have done… they took people who did IT and slapped another hat on them to do cybersecurity. The fundamental problem with this is that there is a conflict of interest.
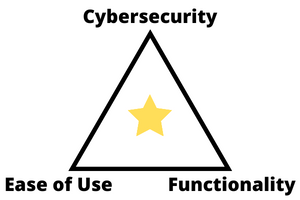
Think of a triangle — Cybersecurity is the top angle, ease of use and functionality are the two bottom angles. In most organizations, you want a balance between the three (cybersecurity, ease of use and functionality). So ultimately, you want to find your operations somewhere in the middle of the triangle.
However, IT people are going to navigate to the bottom two: Ease of use and functionality. Cyberpeople are going to pull you up to the top: Cybersecurity. If you have both types of people in your environment, then you strike a balance. If you only have IT people, then you are naturally going to gravitate to the bottom two categories and away from cybersecurity.
Implementing cybersecurity
If you are willing to balance your organization and move towards cybersecurity, here are some easy wins to implement:
- Multi-Factor Authentication (MFA) with strong passwords (15+ in length and complexity)
- Segmented networks
- A year’s worth of critical data backups
- Extensive logging with alerts
- An aggressive patching program
There are many resources available. Reach out to me for a comprehensive list or visit https://www.cisa.gov.
Facts and Helpful security Tips
Criminal adversaries sit in your environment for an average of six months. Some national state actors sit in your environment until you kick them out. It is also important to put things in place in your environment to trigger on their presence before they rear their ugly heads (e.g. encryption with a ransom note). If I could give you one piece of advice to avoid attacks both personally and professionally is DON’T EVER CLICK LINKS if you can avoid it! If you can’t avoid it, pick up the phone and text/call to verify the link was actually sent to you and is not malicious.
The second advice is use strong passwords of 15 characters or more with at least three degrees of complexity (uppercase, lowercase, numbers, symbols). You should never reuse a password, so a password manager might be the best option for you.
Data drives the way we live. Do your part to secure your data whether it is your personal data or your professional data. Prove to the adversary that they need to look for a softer target than you! Start a cybersecure culture in your life or your organization!
About the Author
Terin Williams serves as the Cyber Security Advisor for the Department of Homeland Security (DHS) at the Cybersecurity and Infrastructure Security Agency (CISA). Terin is responsible for bringing together critical infrastructure owners/operators with federal, state, local, and other stakeholders to maximize collaboration and minimize cyber risk in the State of Ohio.
Prior to this position, Terin was the Chief Information Officer (CIO) for the Ohio Army National Guard who had oversight of the Ohio Guard cyber forces. She was the Chief Information Security Officer (CISO) for the Ohio Army National Guard previous to the CIO position and served as the cyber team lead. Additionally, she serves as the Industrial Defense Sector Lead for the Columbus chapter of INFRAGARD.
A current member of the Army National Guard, she is the Brigade Commander of the first and the only Cyber Brigade in the Army National Guard that spans thirty-one states. She has had multiple deployments and has multiple military awards. She led the national Cyber Shield exercise from 2017 through 2020.
She holds a Master of Arts in National Security and Strategic Studies from the Naval War College and a Master of Science in Computer and Information Systems Security/Information Assurance from the University of Maryland Global Campus (UMGC). She also has a Bachelor of Arts in Chemistry from Case Western Reserve University. Some certifications include (but not limited to): CISSP, CISM, GCIH, GCIA, C|EH, and ISA Cybersecurity Maintenance Specialist.